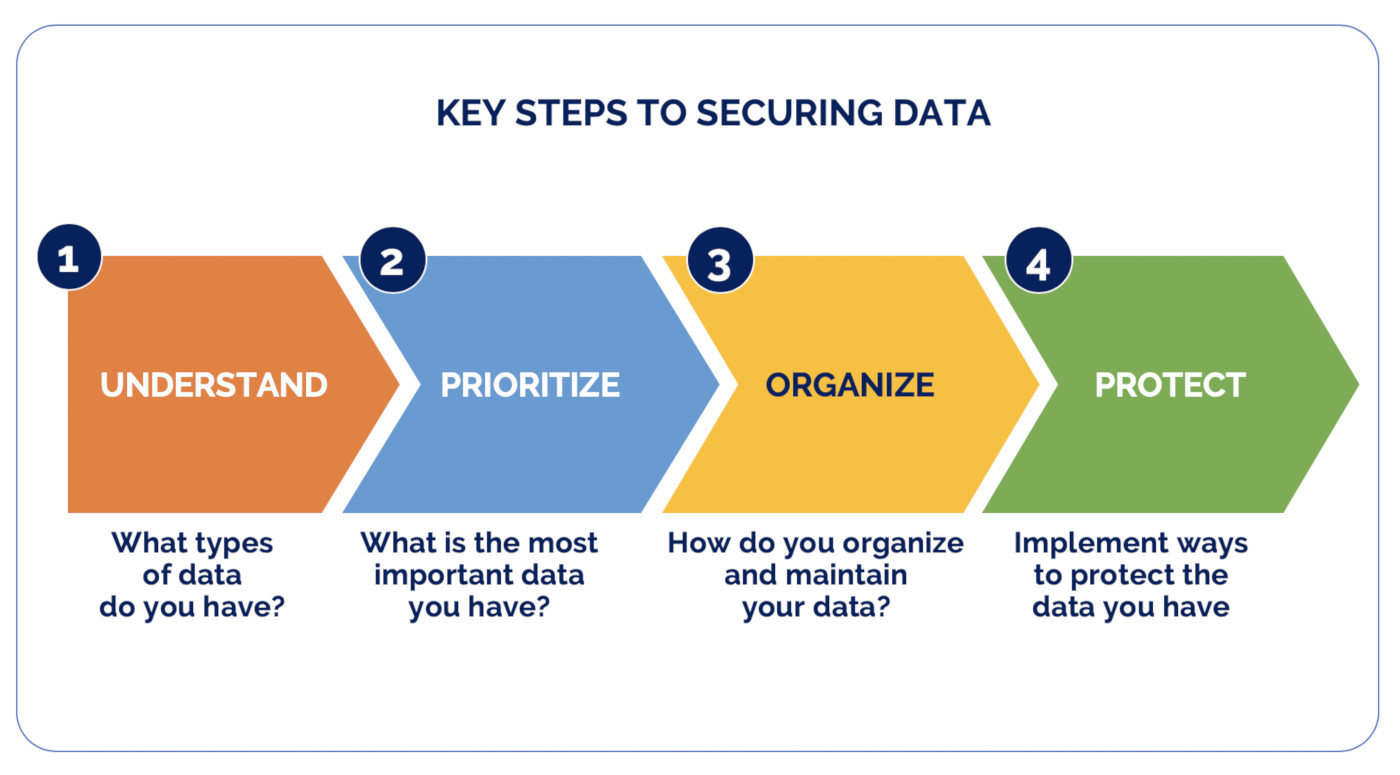
The Definitive Guide to Managed It Services For Law Firms
This is remarkably for the business that enable workers to use their very own phones for carrying out tasks. The support offering firms position their group to safeguard that data as well as assets from hackers or abuse.
It ensures that only safe and secure gadgets will have the ability to do from another location, as they would certainly be capable of protecting the sensitive information of the firm. It describes the on-demand accessibility of computer system sources, including information storage space and also computer power. This happening does not call for any direct energetic monitoring by the individual.
As its benefits are amazing, an increasing number of firms have actually begun shifting to the cloud for holding their data. managed it services melbourne. For keeping their personal info about clients and their client experience (CX) secure, it includes some extraordinary security functions. The technology assistance team handles it well in two means: Ensuring configuring and also managing the cloud system for holding a variety of requisite applications, data monitoring, IT sustain and downtime, Using the full safety and security to what comes under the managed IT services from cyber crooks.
Not known Facts About Managed It Services For Law Firms

Something failed. Wait a minute as well as try again Attempt once more.

Companies are progressively moving their IT infrastructures into the cloud (it service melbourne). Numerous business organizations now operate in multi-cloud environments or use hybrid on-premises and cloud-based IT styles. These complexities necessitate the need for IT sustain solutions to take care of these systems. Cloud computer support is an IT solution that aids companies handle their cloud-based infrastructure.
The Only Guide for It Services Melbourne
Information backup and recuperation assistance include the implementation of information backup solutions, such as cloud-based, disk-based as well as tape-based back-ups. Information back-up and recuperation support Entails testing information recovery options to ensure that they are trusted and reliable in the occasion of a data loss or corruption. IT support is essential for organizations that rely heavily on their information, such as those in the health care as well as finance industries - managed it services melbourne.
Office technology changes quickly as well as obtains more complicated by the year. Whereas the mass of occupational computing when took area within the office walls and inside a safe and secure boundary, today's distributed labor force conducts business from homes, coffeehouse, cars literally dig this anywhere with internet access. Supporting and securing the myriad devices and access factors workers now count on to stay productive has actually developed a lot even more help IT groups that typically are currently spread as well slim.
Organizations resort to managed solutions service providers (MSPs) for a variety of my review here factors, however a lot of frequently, they are employed by organizations with no internal IT team or those that want to utilize their internal IT experts to focus on certain initiatives rather than functional duties for taking care of modern technology. MSPs provide a large variety of services from the fundamentals such as assistance workdesk assistance and keeping IT equipment and also services functioning all the means as much as providing the complete collection of IT abilities, including cyber protection, web connectivity, application assistance, data backups, as well as disaster recuperation.

It Services Melbourne Fundamentals Explained
Handled IT services are far from one-size-fits-all, so partnering with an MSP who Resources understands your company and is actively bought aiding you satisfy your objectives is important.
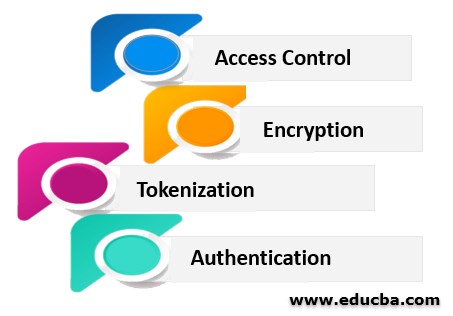
Potential risks outside the network are protected against, making sure that an organization's delicate information remains inside. Organizations can go further by specifying additional interior borders within their network, which can give improved security and accessibility control. Gain access to control defines the individuals or teams as well as the devices that have access to network applications and also systems thus rejecting unauthorized accessibility, and maybe threats.
A susceptability is a bent circumstances in a software program system and an exploit is an assault that leverages that vulnerability to obtain control of that system. When a make use of is introduced, there is usually a window of possibility for attackers to manipulate that vulnerability prior to the safety patch is used.
Sandboxing is a cybersecurity method where you run code or open files in a risk-free, isolated setting on a host equipment that resembles end-user operating settings. Sandboxing observes the documents or code as they are opened as well as searches for destructive habits to prevent hazards from jumping on the network. Malware in data such as PDF, Microsoft Word, Excel and also Power, Point can be safely identified and blocked before the data get to an innocent end user.